Important: Beware of Punycode Phishing Scams Targeting Crypto Users

In the past few weeks we have noticed an increased phishing scam attack rate using…
The post Important: Beware of Punycode Phishing Scams Targeting Crypto Users first appeared on Crypto Beat News.
In the past few weeks we have noticed an increased phishing scam attack rate using sophisticated Punycode email addresses. These attacks exploit Unicode characters that resemble standard ASCII characters, creating deceptive email addresses and domain names that are difficult to distinguish from legitimate ones.
And despite millions of phishing emails being intercepted by spam filters and users becoming more adept due to well-defined cybersecurity programs, phishing remains a persistent threat. Spear phishers continually develop new and sophisticated methods to increase their success rates.
In the past Kraken was already targeted as you can read here, but the problem is still there with lots of other services being selected for this type of refined scams.
The emails targeted for phishing scams are often harvested from various sources, including social media platforms like Facebook or X. Despite Facebook’s claims that scraping email addresses is not feasible, it is possible to extract thousands of email addresses from public pages and profiles. These harvested emails are then used by scammers to launch targeted phishing attacks, often leveraging Punycode to disguise malicious domains.
Here’s what you need to know to protect your crypto assets from these scams.
Table of contents
How Punycode Phishing Works
Punycode is used to encode Unicode characters in the ASCII character set, which is required by the Domain Name System (DNS). Scammers exploit this to craft email addresses and domain names that appear almost identical to legitimate ones but are actually different.
Example:
- Original Domain: example.com
- Phishing Domain: еxample.com (with the first “e” replaced by the Cyrillic “е”)
Visually, these domains look the same, but their actual representations differ:
- Phishing Domain in Punycode: xn--xample-9ua.com
How Scammers Use Punycode
Attackers may send an email from support@xn--xample-9ua.com, which your email client displays as support@еxample.com. This tricks users into thinking the email is from a trusted source, leading them to click on malicious links or provide sensitive information, potentially compromising their crypto wallets.
Detection Techniques
To detect and prevent Punycode phishing attempts, you might want to consider these methods:
- Domain Name Normalization:
- Convert Punycode domains to their Unicode equivalents and check for visually similar characters.
- Example: Compare
xn--xample-9ua.comtoexample.com.
- Whitelist and Blacklist:
- Maintain lists of trusted and known malicious domains.
- Compare incoming email addresses against these lists.
- User Education:
- Inform users about the risks of Punycode phishing.
- Encourage vigilance regarding slight differences in email addresses and domain names.
- Automated Tools:
- Use automated tools and services that detect and flag Punycode domains.
- Many security solutions offer this feature as part of their phishing protection suites.
- Email Filters:
- Configure email filters to detect and flag emails from Punycode domains similar to trusted domains.
Practical Example
Here are the steps for detecting a Punycode phishing email:
- Check the From Address:
- Inspect the sender’s email address carefully. Look for unusual characters or the
xn--prefix indicating a Punycode domain.
- Inspect the sender’s email address carefully. Look for unusual characters or the
- Convert Punycode:
- Use tools like Punycode Converter to convert the Punycode back to its Unicode representation and manually verify it.
- Automated Check:
- Implement a script or use a security tool that scans incoming emails for Punycode domains and compares them against known trusted domains.
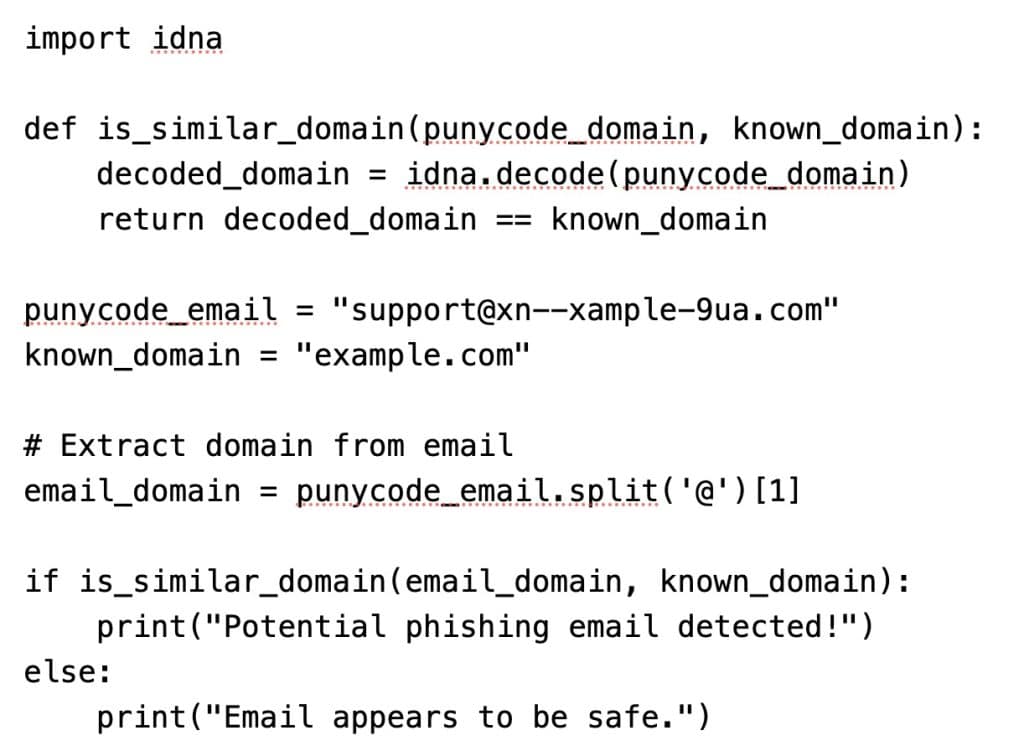
Example Python Script for Detection
Here’s a simple Python script to help detect potential Punycode phishing domains:
Stay Very Vigilant
Basically, you should never click on an email you didn’t trigger yourself. And you should never connect your crypto wallet to any service via email. If you receive a suspicious email, do not click on any links or download attachments.
As an extra for the techsavy readers, the below video explores and demonstrates advanced techniques such as typosquatting, doppelganger domains, and IDN homograph attacks, all of which pose significant risks even to modern, fully patched browsers and email systems. For those wondering what this all means:
- Typosquatting: Registering misspelled versions of popular domains to trick users.
- Doppelganger Domains: Creating domains that are visually similar to legitimate ones.
- IDN Homograph Attacks: As explained in our article this is the use of Unicode characters that look like standard ASCII characters to create deceptive domain names.
The post Important: Beware of Punycode Phishing Scams Targeting Crypto Users first appeared on Crypto Beat News.
Since you’re here …
… we have a small favour to ask. More people are reading Side-Line Magazine than ever but advertising revenues across the media are falling fast. Unlike many news organisations, we haven’t put up a paywall – we want to keep our journalism as open as we can - and we refuse to add annoying advertising. So you can see why we need to ask for your help.
Side-Line’s independent journalism takes a lot of time, money and hard work to produce. But we do it because we want to push the artists we like and who are equally fighting to survive.
If everyone who reads our reporting, who likes it, helps fund it, our future would be much more secure. For as little as 5 US$, you can support Side-Line Magazine – and it only takes a minute. Thank you.
The donations are safely powered by Paypal.



